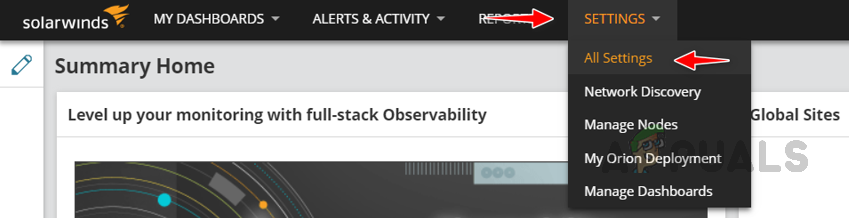
To avoid such critical issues and to be independent, we can use Solarwinds NCM to identify the vulnerabilities in the firmware and fix them. Solarwinds NCM has an automated Firmware Vulnerability Scanning feature and Firmware Upgrade option to apply patches with the latest Firmwares. To know more about Solarwinds NCM, click on this link.
How Firmware Vulnerability Scanning Works
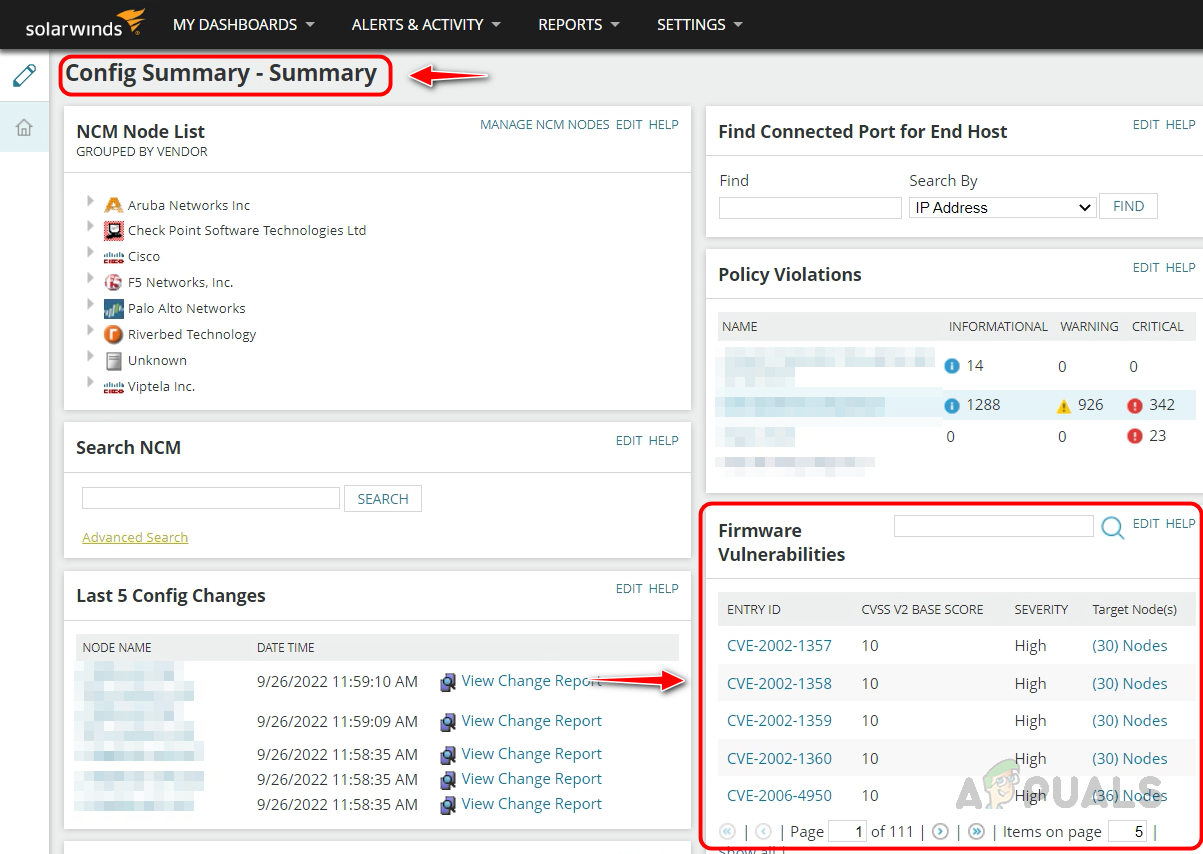
NCM gets the firmware vulnerability warning data from the National Institute of Standards and Technology (NIST). NCM uses this data to compare with nodes currently monitored by Solarwinds NCM. If the vulnerability data matches any of the nodes, it will be reported in the Config Summary page of the Firmware Vulnerabilities widget.
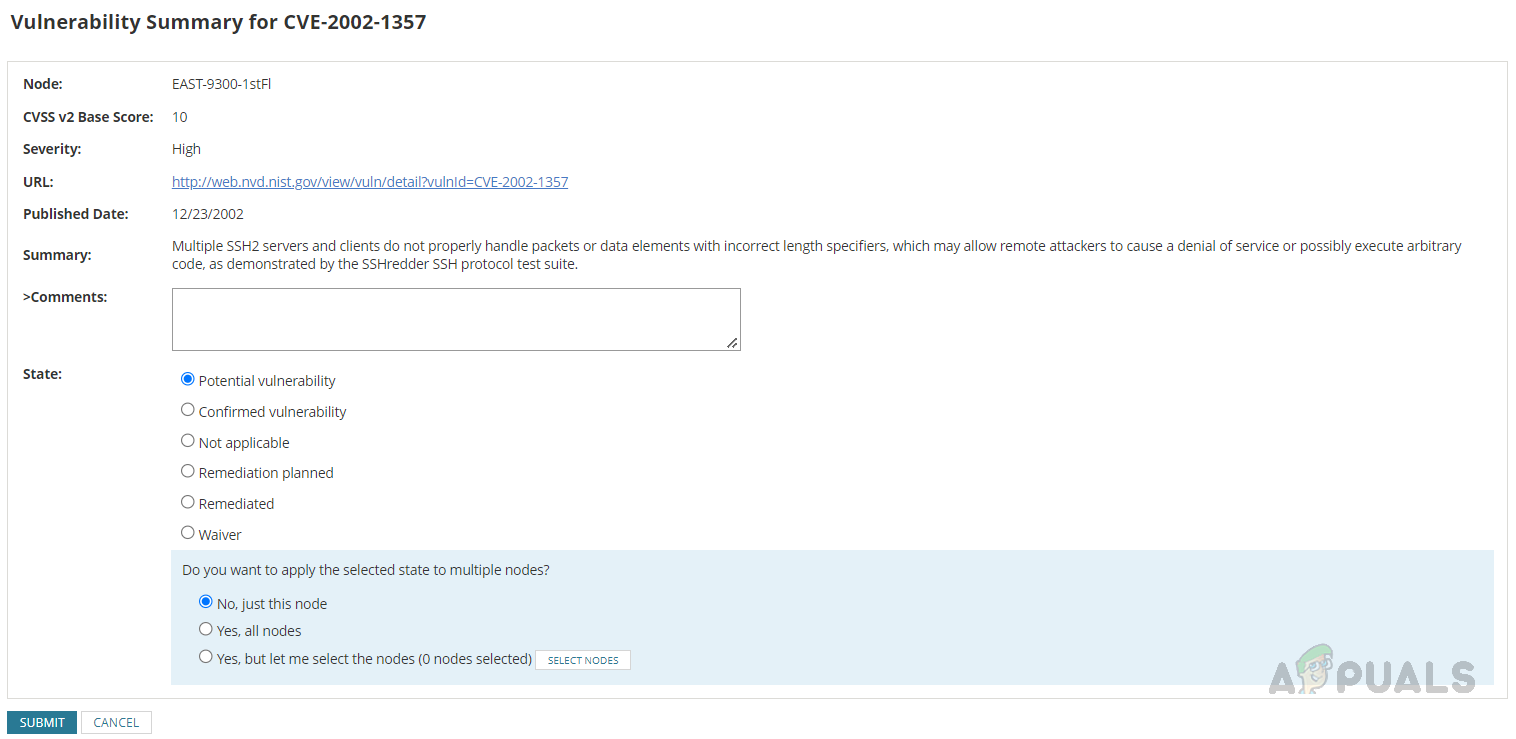
We can see CVE ID, Score, Severity, and the nodes have these vulnerabilities. If we click on the CVE ID, that will take us to the summary page where we can see the vulnerability summary.
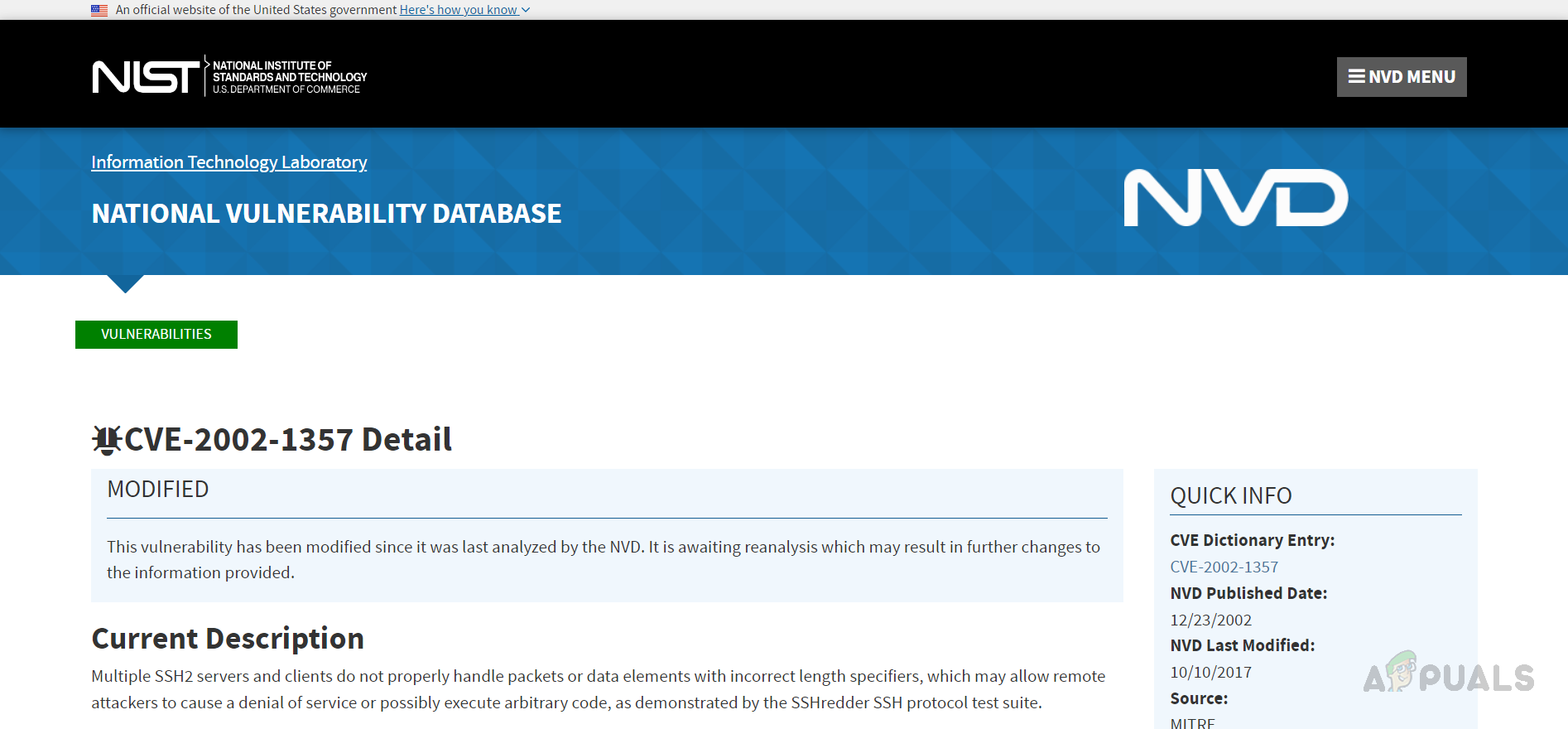
If we click on the NIST URL, it will take us to the NIST page for the vulnerability, where we can find more details about the reported vulnerability.
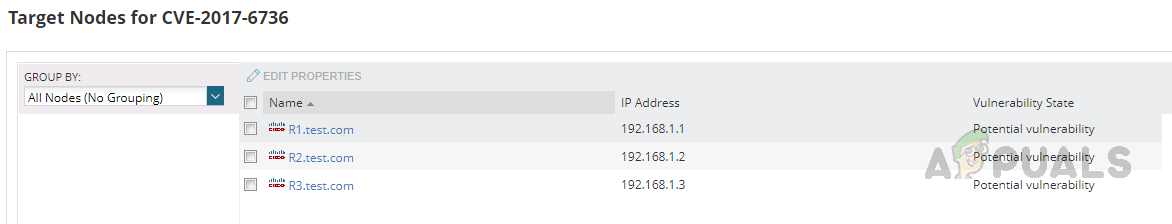
To get the nodes affected by this vulnerability, click on the Node(s) under Target Node(s)
Currently, Firmware Vulnerability scanning support only the following device types.
Cisco IOSCisco Adaptive Security Appliance (ASA)Cisco NexusJuniper
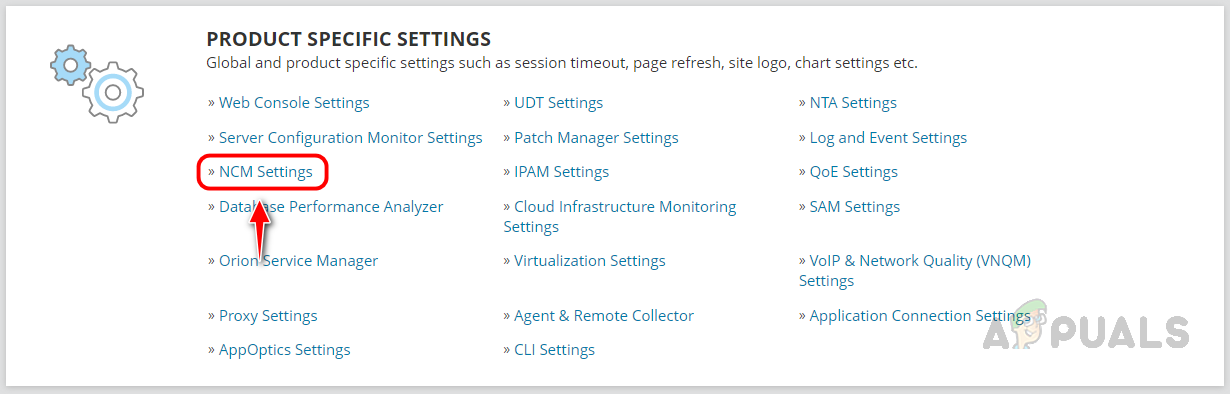
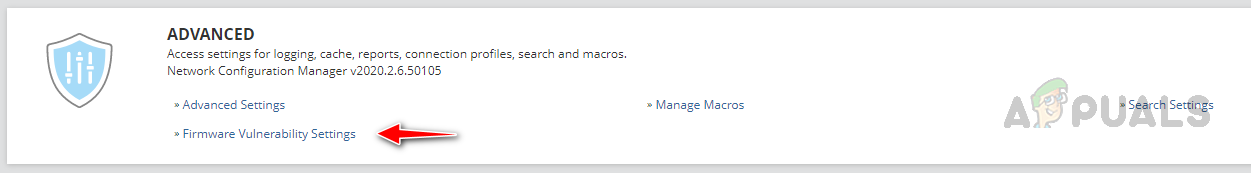
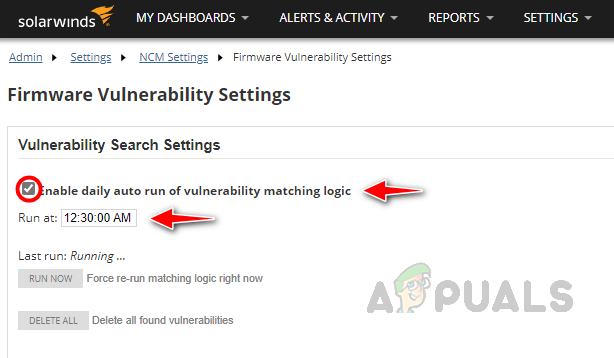
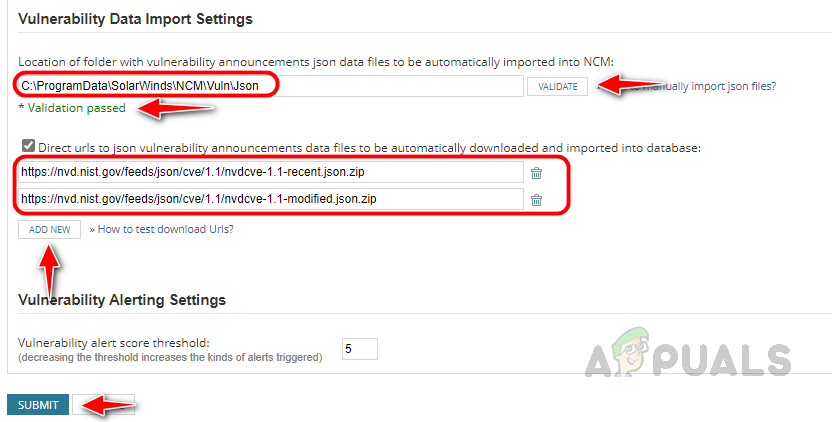
We need to configure the Firmware Vulnerability settings to get the automated vulnerability reports. Let’s see how to configure the settings below.
Configuring Firmware Vulnerability Settings
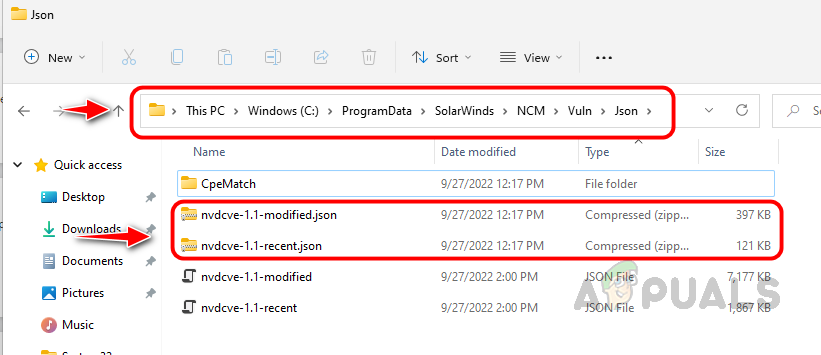
Follow the below steps to configure the Firmware Vulnerability Settings, by configuring these settings, NCM can download the vulnerability data to compare with the monitored devices. We have set up the scanning feature. NCM will perform the scans at the scheduled time and will show the report on the Config Summary page as shown earlier. Based on the scan report, we need to apply patches. Now let’s see how to set up the Firmware Upgrade feature to apply patches.
Configuring Firmware Upgrade Feature
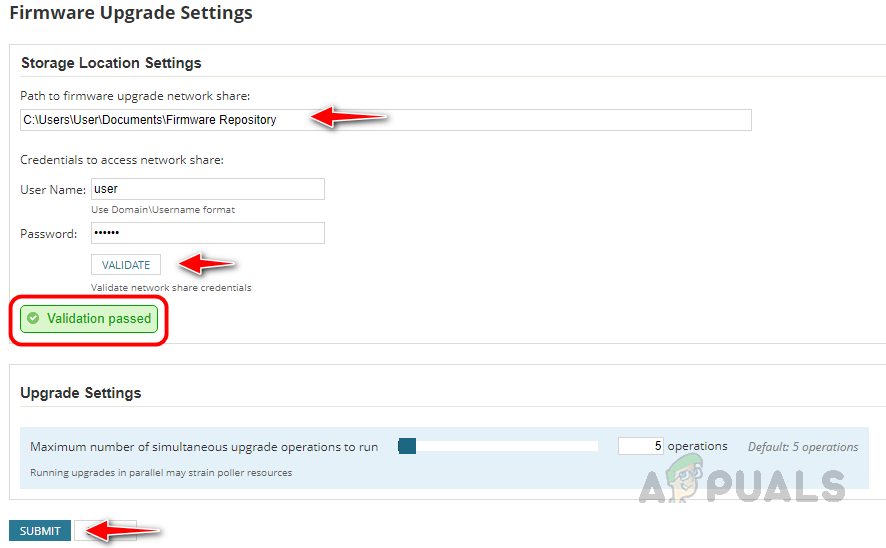
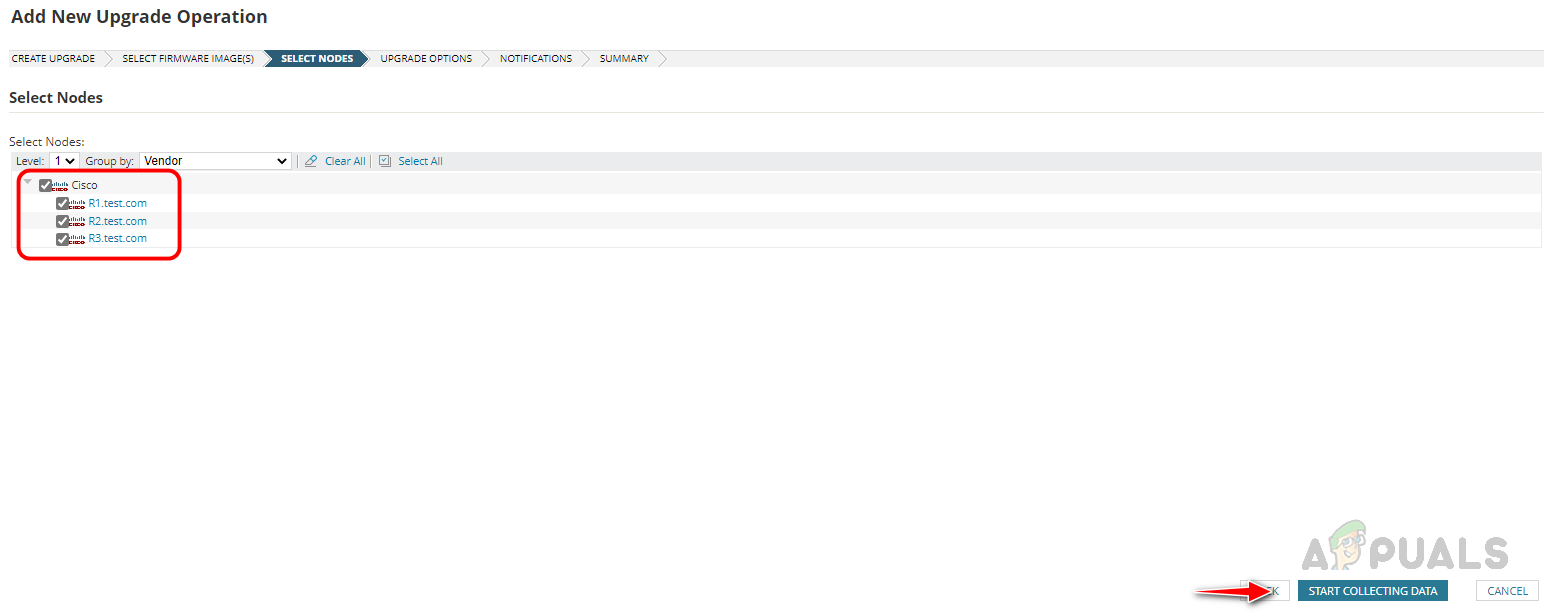
The Firmware Upgrade feature in NCM can be used to upgrade the devices with the latest firmware to protect the devices from vulnerabilities. Multiple devices can be added to the firmware upgrade job and we can run multiple firmware upgrade jobs simultaneously. To configure the firmware upgrade job first we need to do some initial setup. Follow the below steps to complete the initial setup.
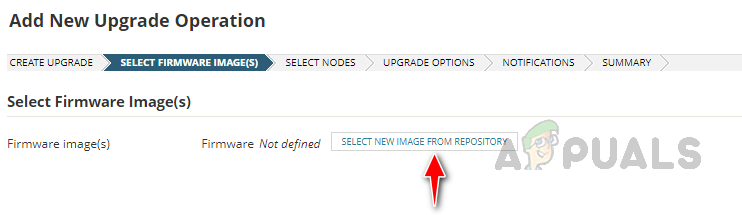
Step 1: Map the Storage Location of Firmware Images
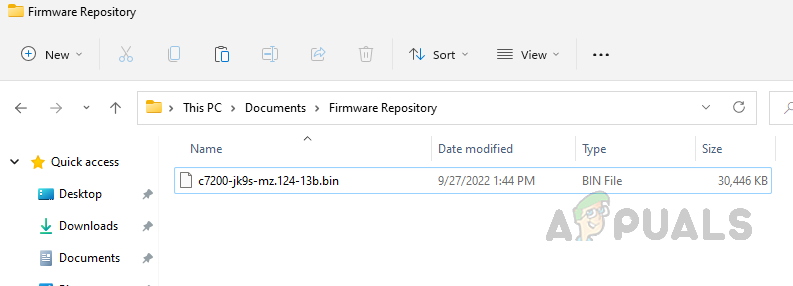
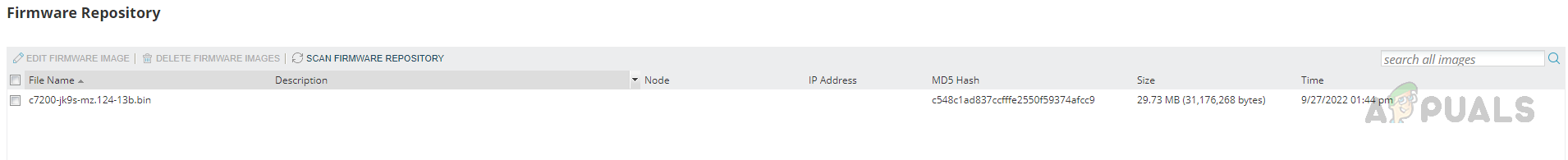
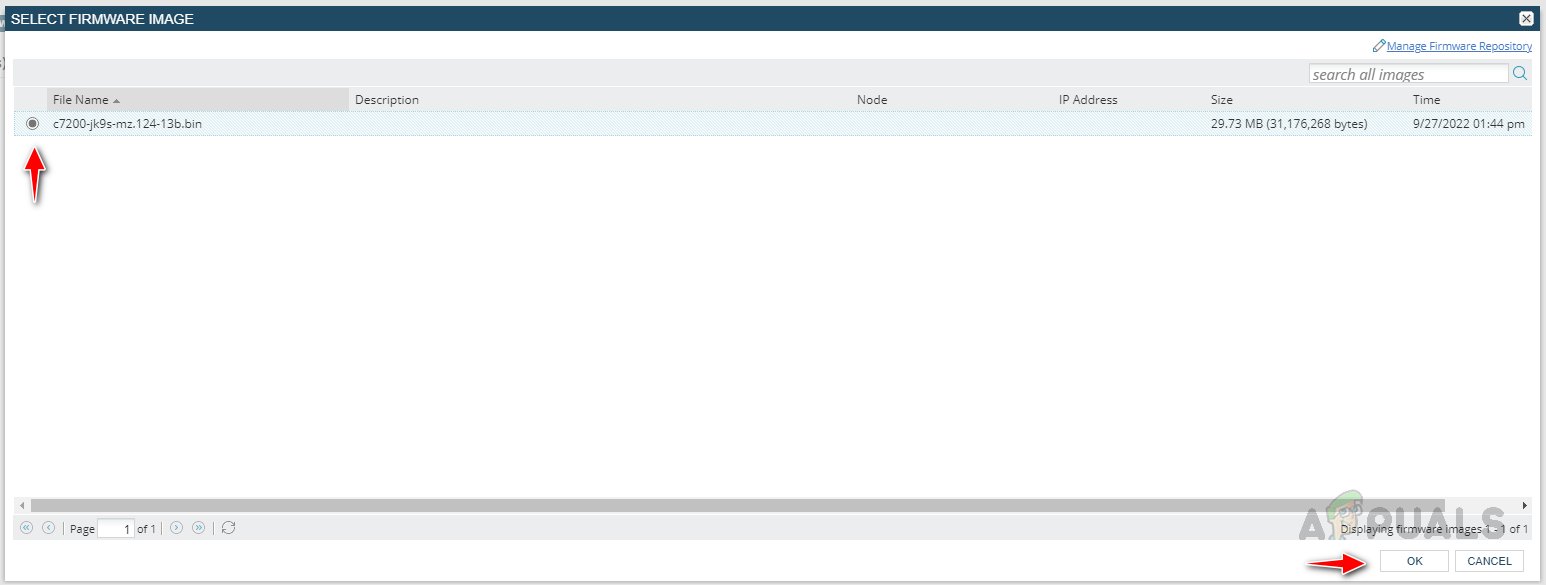
Step 2: Place the Firmware Images in Storage Location
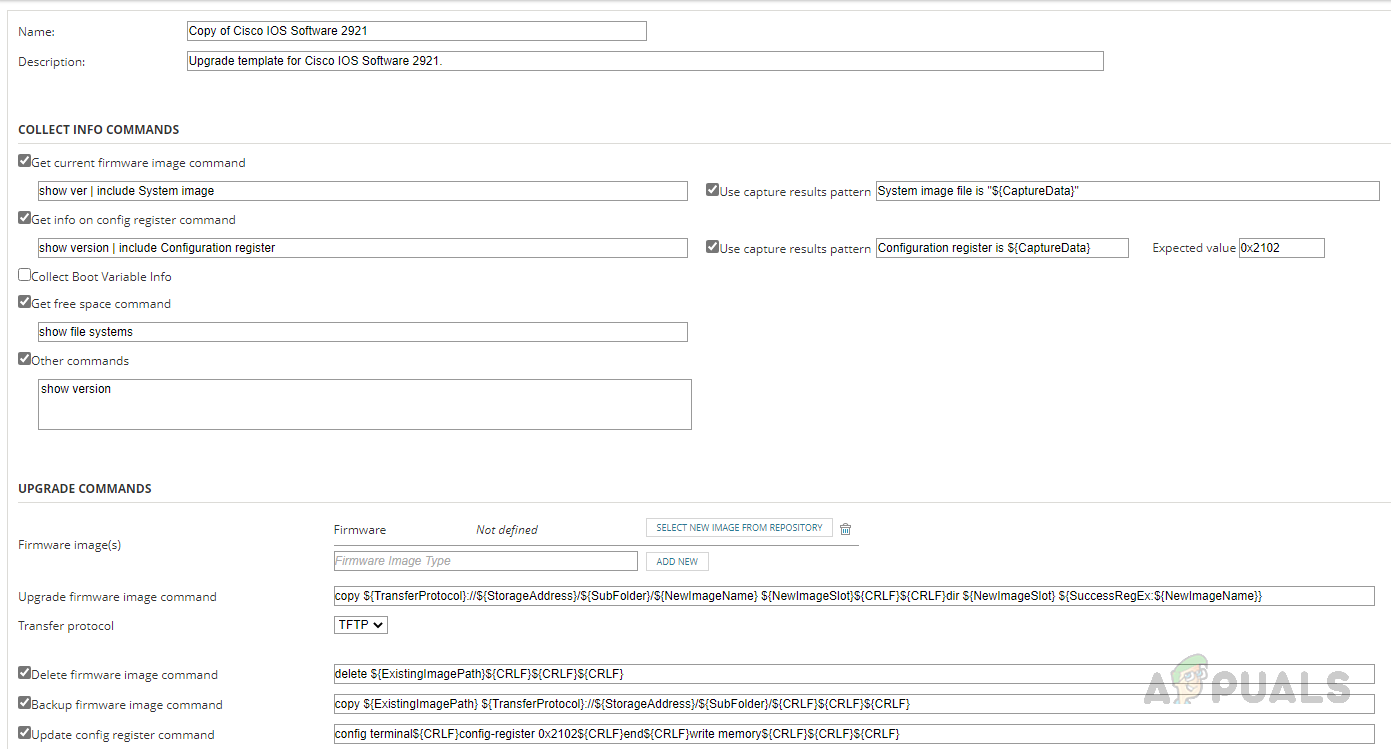
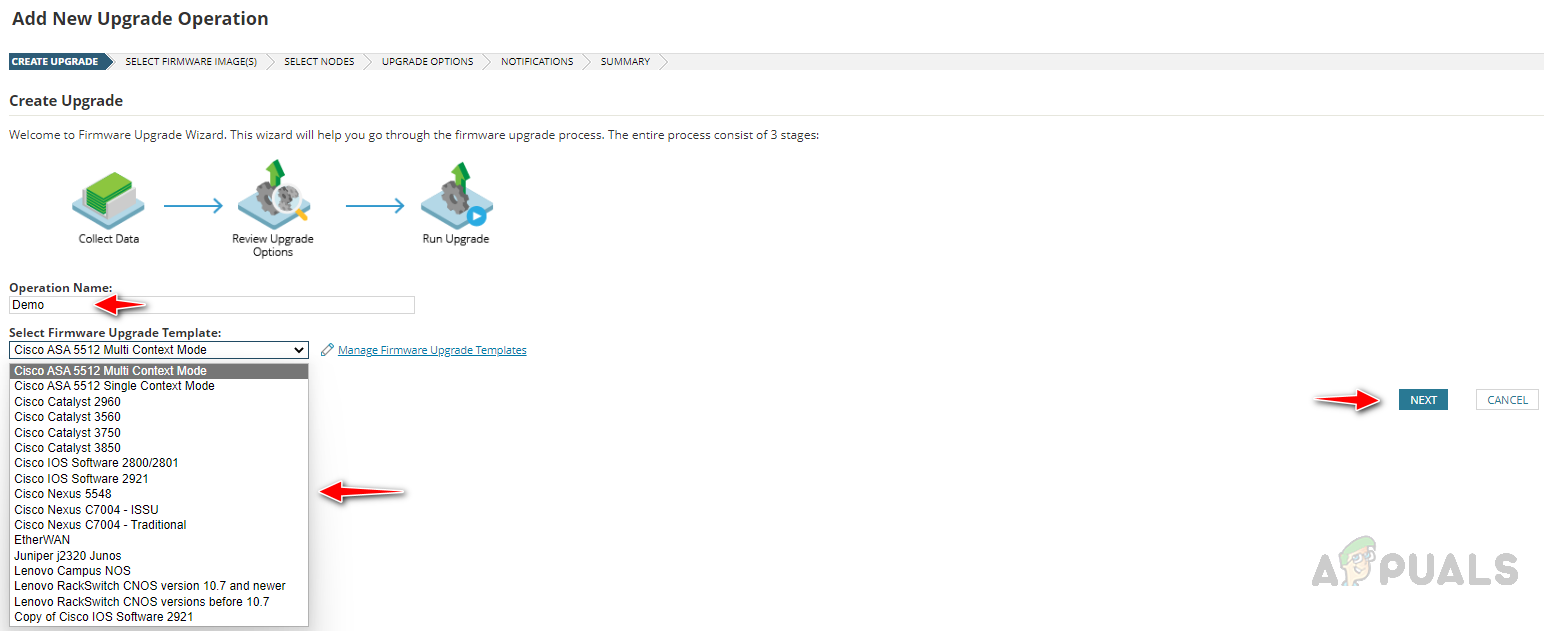
Step 3: Configure Firmware Upgrade Template
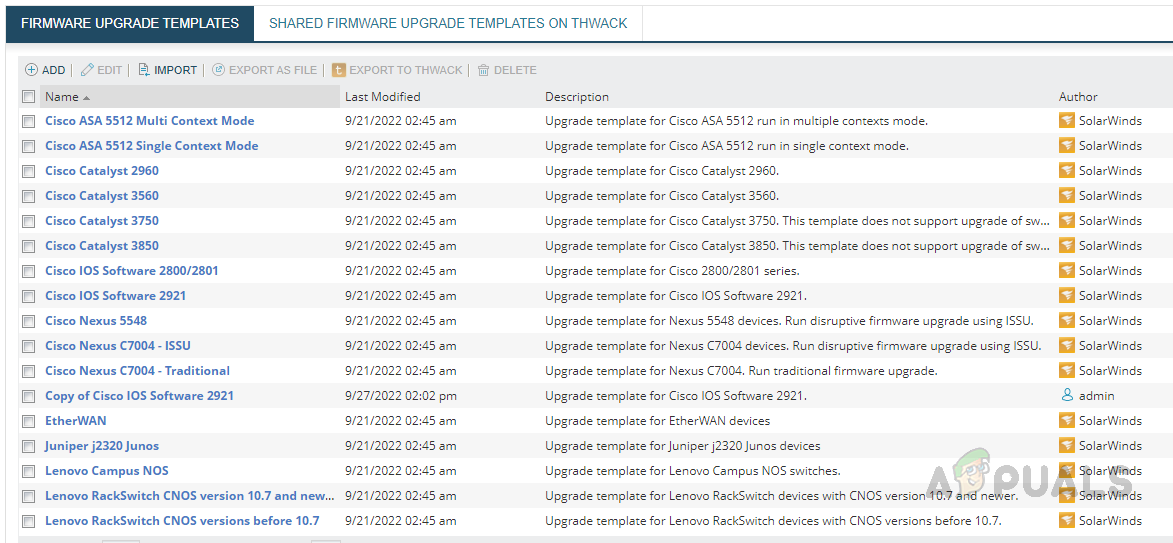
This is the last step of our initial setup. Solarwinds NCM comes up with pre-configured firmware templates, we can use them in our firmware upgrade jobs based on the device and firmware version. To check the firmware upgrade templates, follow the below steps. We have set up all the initial requirements to configure the firmware upgrade job. Now let’s see how to set up the firmware upgrade job.
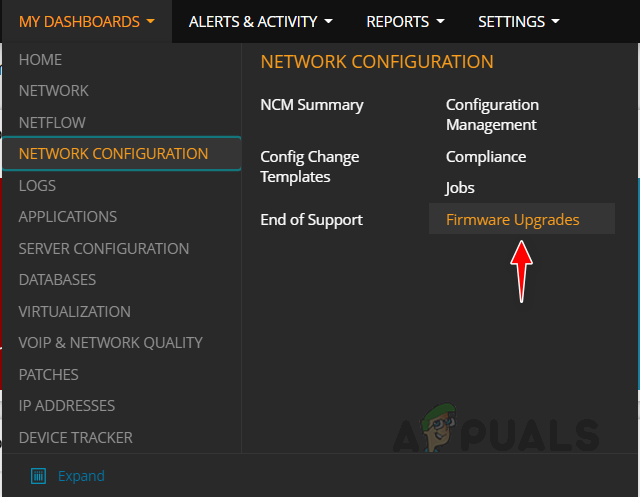
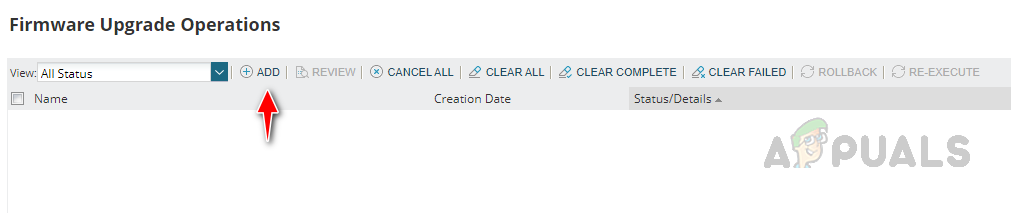
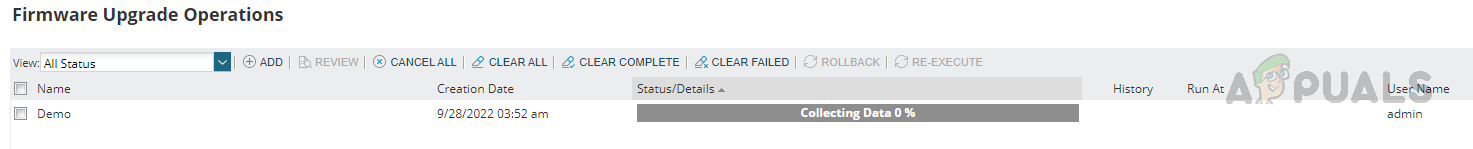
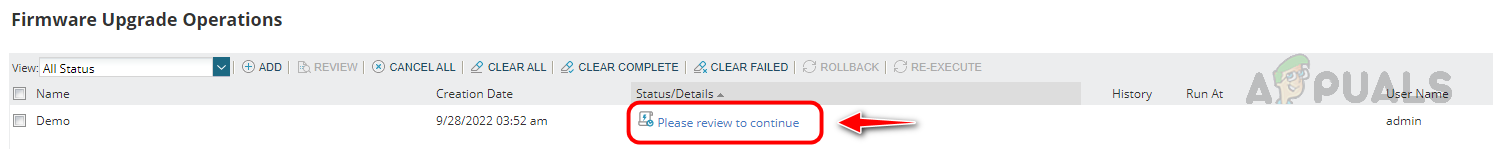
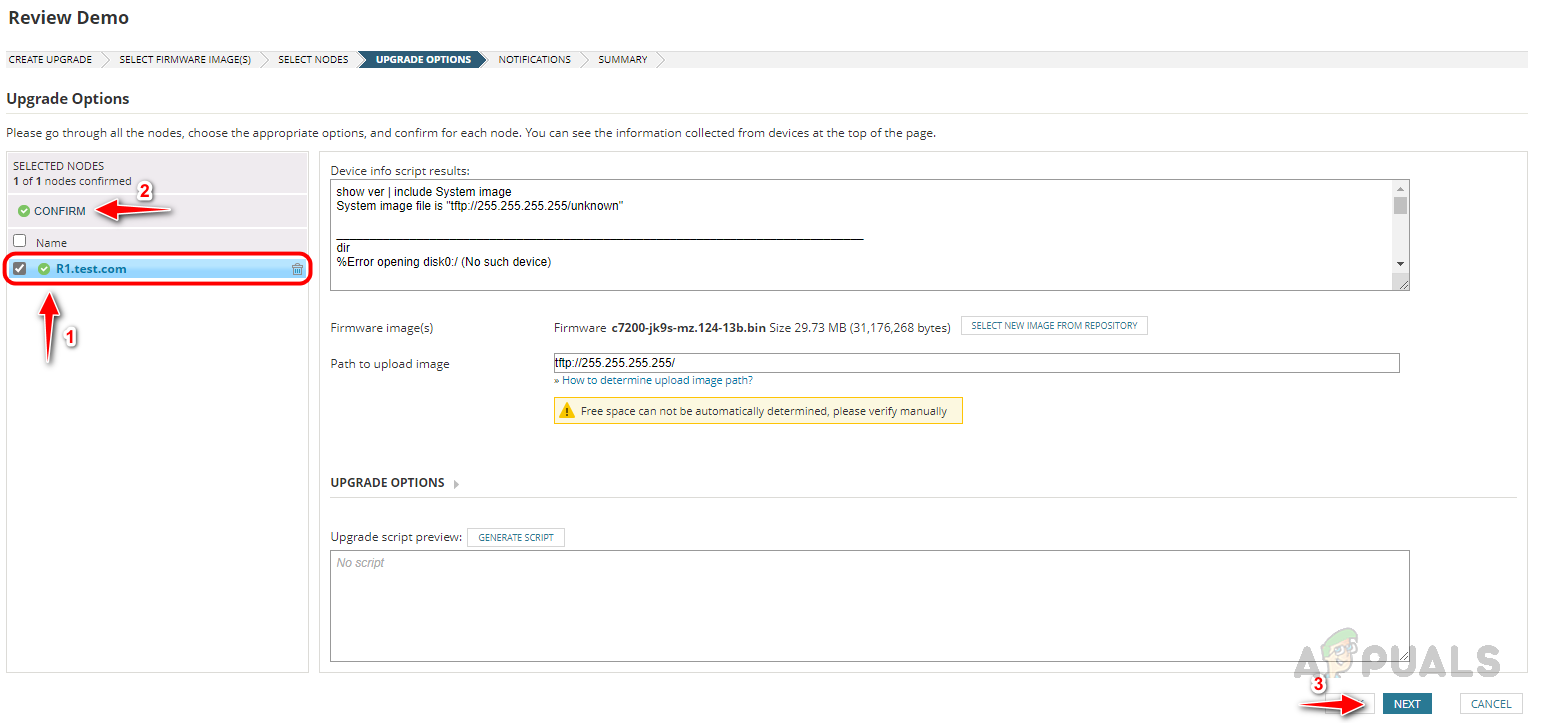
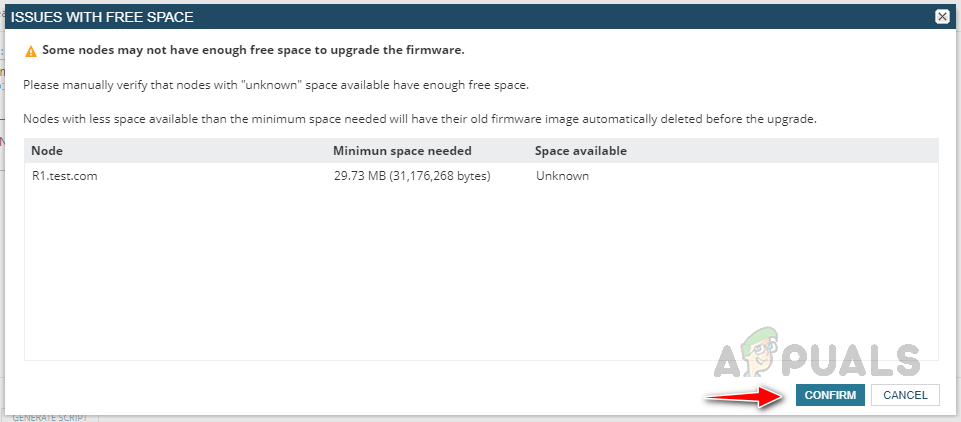
Configuring Firmware Upgrade Job
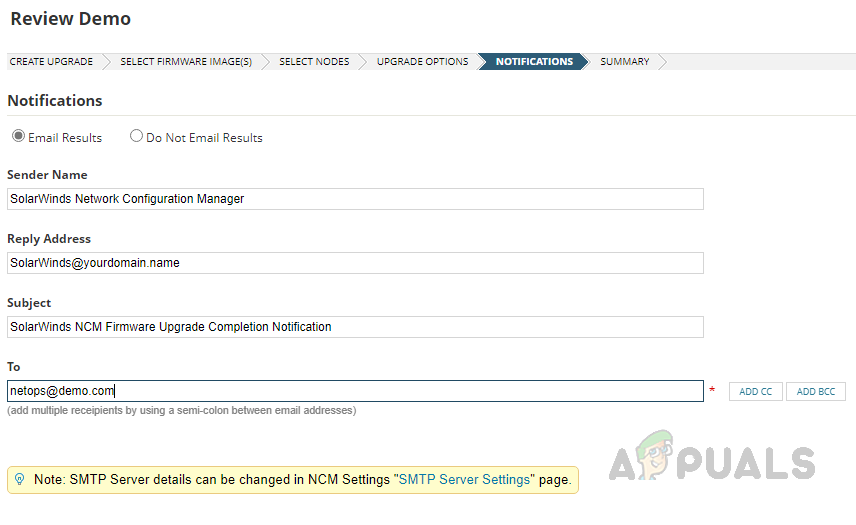
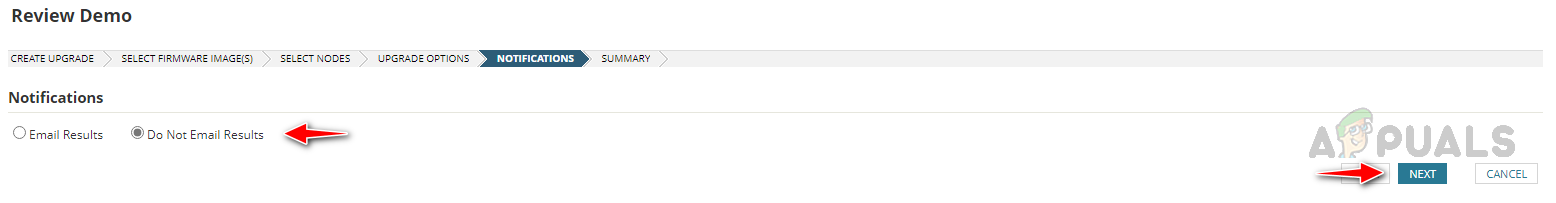
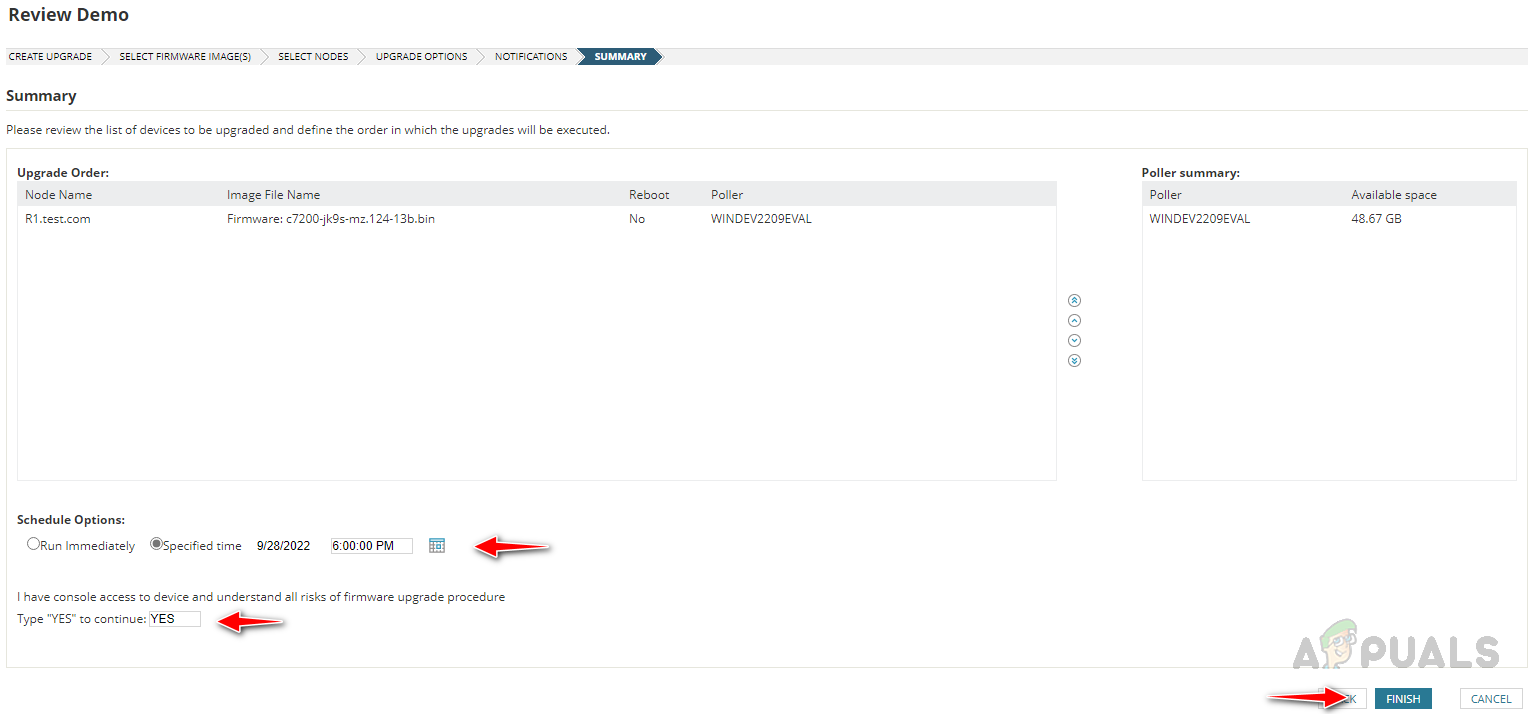
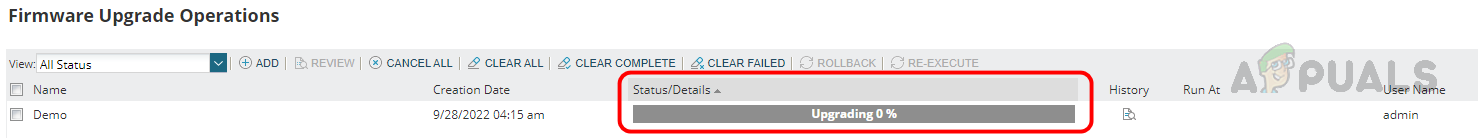
Follow the below steps to configure the firmware upgrade job. This is how we can use the Firmware Vulnerability Scanning and Firmware Upgrade feature in Solarwinds NCM to detect and fix vulnerabilities with the latest firmware.
How to Automate Network Audits for Network Compliance using Solarwinds NCM?How to Automate Network Configuration Backup Using SolarWinds NCMHow to Identify Recursive and Empty Groups in Active Directory using Access…Witcher 3 Switch Patch 3.6: Improved Graphics and the option To Import Saves…